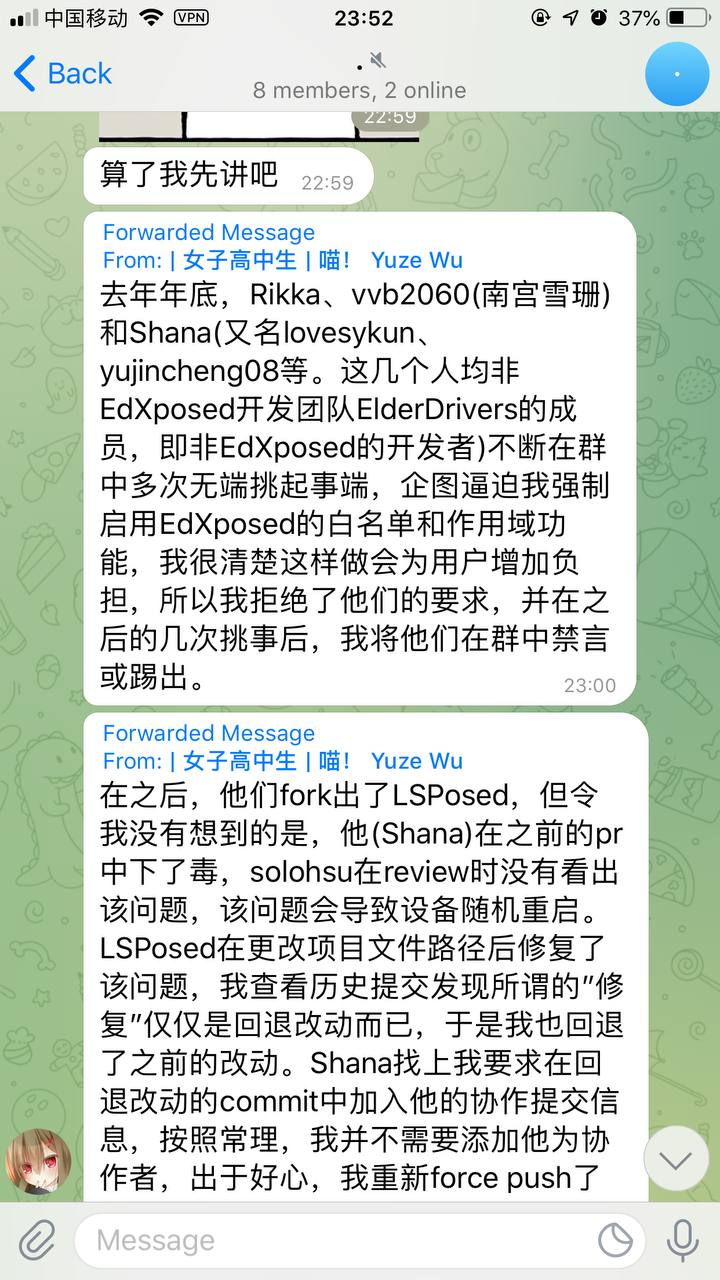
其实写这个主要是有人邀请……那就这样得了,双线并行。
内存取证
对应嘛题
去年三校训练赛那边出了道内存取证题(当时用volatility 2,觉得比3好用),然后西湖论剑那边也出了道(虽然我没做出来)
- 三校联合内部训练赛 GoodRAM
- (说起来很丢人
,虽然隔壁VNCTF那边更丢人)西湖论剑 (原题目忘了)CharlieBrownPC
冷笑话,西湖论剑那边还出了道要用到夜神模拟器的题,但那边给的镜像根本没法导入,甚至上我那Toshiba Satellite L750也一样,虽然那个好像不算内存取证,但没办法,我根本无法判断题型。
这俩题基本都是取证Windows系统的内存镜像,所以直接按Windows说得了,邪教终究是邪教 Arch YES!
嘛是内存取证
我个人理解是提取一个人电脑内存中的东西后用特定工具进行分析,通俗一点说的话则是相当于拿你一根头发丝在那硬分析。
当然就这么写的话肯定不太准确,所以……在主机存活时发现系统被入侵,然后直接把机器的运行内存dump下来,对运行内存进行分析,还原一些进程的中的信息。
……妈的真不如自己总结。
用啥取证
用啥提取镜像
- DumpIt(Windows)(嗯,goodRAM题目就是用这损玩意儿整来的)
- Windows 快速启动(冷提醒,快速启动原理就是恢复内存镜像)
- Windows 任务管理器(创建转储文件)
用啥日镜像
- Volatility工具(2和3版本,这俩不一样,还有,volatility3别在Arch community源下!自己去GitHub下二进制文件!链接给的官网早就不更新了!)
剩下的freebuf有,给俩链接,虽然这句话并不能写在PPT里
https://www.freebuf.com/column/186799.html
https://www.freebuf.com/articles/network/265797.html
工具咋用
DumpIt
这玩意儿一笔带过得了,没必要玩这么大
点开它,等它跑完,看不懂英语的自备翻译
Volatility 2(是的,2和3命令完全不同)
冷提醒,忘记命令的时候直接在终端跑一下就行,它会自动告诉你咋用
AUR那边缺模块
user@TUSKEDEV ~> ./volatility -h
Volatility Foundation Volatility Framework 2.6
Usage: Volatility - A memory forensics analysis platform.
Options:
-h, --help list all available options and their default values.
Default values may be set in the configuration file
(/etc/volatilityrc)
--conf-file=/home/user/.volatilityrc
User based configuration file
-d, --debug Debug volatility
--plugins=PLUGINS Additional plugin directories to use (colon separated)
--info Print information about all registered objects
--cache-directory=/home/user/.cache/volatility
Directory where cache files are stored
--cache Use caching
--tz=TZ Sets the (Olson) timezone for displaying timestamps
using pytz (if installed) or tzset
-f FILENAME, --filename=FILENAME
Filename to use when opening an image
--profile=WinXPSP2x86
Name of the profile to load (use --info to see a list
of supported profiles)
-l LOCATION, --location=LOCATION
A URN location from which to load an address space
-w, --write Enable write support
--dtb=DTB DTB Address
--shift=SHIFT Mac KASLR shift address
--output=text Output in this format (support is module specific, see
the Module Output Options below)
--output-file=OUTPUT_FILE
Write output in this file
-v, --verbose Verbose information
-g KDBG, --kdbg=KDBG Specify a KDBG virtual address (Note: for 64-bit
Windows 8 and above this is the address of
KdCopyDataBlock)
--force Force utilization of suspect profile
-k KPCR, --kpcr=KPCR Specify a specific KPCR address
--cookie=COOKIE Specify the address of nt!ObHeaderCookie (valid for
Windows 10 only)
Supported Plugin Commands:
amcache Print AmCache information
apihooks Detect API hooks in process and kernel memory
atoms Print session and window station atom tables
atomscan Pool scanner for atom tables
auditpol Prints out the Audit Policies from HKLM\SECURITY\Policy\PolAdtEv
bigpools Dump the big page pools using BigPagePoolScanner
bioskbd Reads the keyboard buffer from Real Mode memory
cachedump Dumps cached domain hashes from memory
callbacks Print system-wide notification routines
clipboard Extract the contents of the windows clipboard
cmdline Display process command-line arguments
cmdscan Extract command history by scanning for _COMMAND_HISTORY
connections Print list of open connections [Windows XP and 2003 Only]
connscan Pool scanner for tcp connections
consoles Extract command history by scanning for _CONSOLE_INFORMATION
crashinfo Dump crash-dump information
deskscan Poolscaner for tagDESKTOP (desktops)
devicetree Show device tree
dlldump Dump DLLs from a process address space
dlllist Print list of loaded dlls for each process
driverirp Driver IRP hook detection
drivermodule Associate driver objects to kernel modules
driverscan Pool scanner for driver objects
dumpcerts Dump RSA private and public SSL keys
dumpfiles Extract memory mapped and cached files
dumpregistry Dumps registry files out to disk
editbox Displays information about Edit controls. (Listbox experimental.)
envars Display process environment variables
eventhooks Print details on windows event hooks
evtlogs Extract Windows Event Logs (XP/2003 only)
filescan Pool scanner for file objects
gahti Dump the USER handle type information
gditimers Print installed GDI timers and callbacks
gdt Display Global Descriptor Table
getservicesids Get the names of services in the Registry and return Calculated SID
getsids Print the SIDs owning each process
handles Print list of open handles for each process
hashdump Dumps passwords hashes (LM/NTLM) from memory
hibinfo Dump hibernation file information
hivedump Prints out a hive
hivelist Print list of registry hives.
hivescan Pool scanner for registry hives
hpakextract Extract physical memory from an HPAK file
hpakinfo Info on an HPAK file
idt Display Interrupt Descriptor Table
iehistory Reconstruct Internet Explorer cache / history
imagecopy Copies a physical address space out as a raw DD image
imageinfo Identify information for the image
impscan Scan for calls to imported functions
joblinks Print process job link information
kdbgscan Search for and dump potential KDBG values
kpcrscan Search for and dump potential KPCR values
ldrmodules Detect unlinked DLLs
lsadump Dump (decrypted) LSA secrets from the registry
machoinfo Dump Mach-O file format information
malfind Find hidden and injected code
mbrparser Scans for and parses potential Master Boot Records (MBRs)
memdump Dump the addressable memory for a process
memmap Print the memory map
messagehooks List desktop and thread window message hooks
mftparser Scans for and parses potential MFT entries
moddump Dump a kernel driver to an executable file sample
modscan Pool scanner for kernel modules
modules Print list of loaded modules
multiscan Scan for various objects at once
mutantscan Pool scanner for mutex objects
notepad List currently displayed notepad text
objtypescan Scan for Windows object type objects
patcher Patches memory based on page scans
poolpeek Configurable pool scanner plugin
printkey Print a registry key, and its subkeys and values
privs Display process privileges
procdump Dump a process to an executable file sample
pslist Print all running processes by following the EPROCESS lists
psscan Pool scanner for process objects
pstree Print process list as a tree
psxview Find hidden processes with various process listings
qemuinfo Dump Qemu information
raw2dmp Converts a physical memory sample to a windbg crash dump
screenshot Save a pseudo-screenshot based on GDI windows
servicediff List Windows services (ala Plugx)
sessions List details on _MM_SESSION_SPACE (user logon sessions)
shellbags Prints ShellBags info
shimcache Parses the Application Compatibility Shim Cache registry key
shutdowntime Print ShutdownTime of machine from registry
sockets Print list of open sockets
sockscan Pool scanner for tcp socket objects
ssdt Display SSDT entries
strings Match physical offsets to virtual addresses (may take a while, VERY verbose)
svcscan Scan for Windows services
symlinkscan Pool scanner for symlink objects
thrdscan Pool scanner for thread objects
threads Investigate _ETHREAD and _KTHREADs
timeliner Creates a timeline from various artifacts in memory
timers Print kernel timers and associated module DPCs
truecryptmaster Recover TrueCrypt 7.1a Master Keys
truecryptpassphrase TrueCrypt Cached Passphrase Finder
truecryptsummary TrueCrypt Summary
unloadedmodules Print list of unloaded modules
userassist Print userassist registry keys and information
userhandles Dump the USER handle tables
vaddump Dumps out the vad sections to a file
vadinfo Dump the VAD info
vadtree Walk the VAD tree and display in tree format
vadwalk Walk the VAD tree
vboxinfo Dump virtualbox information
verinfo Prints out the version information from PE images
vmwareinfo Dump VMware VMSS/VMSN information
volshell Shell in the memory image
windows Print Desktop Windows (verbose details)
wintree Print Z-Order Desktop Windows Tree
wndscan Pool scanner for window stations
yarascan Scan process or kernel memory with Yara signaturesVolatility 3
user@TUSKEDEV ~> vol
Volatility 3 Framework 2.4.2
usage: volatility [-h] [-c CONFIG] [--parallelism [{processes,threads,off}]]
[-e EXTEND] [-p PLUGIN_DIRS] [-s SYMBOL_DIRS] [-v] [-l LOG]
[-o OUTPUT_DIR] [-q] [-r RENDERER] [-f FILE]
[--write-config] [--save-config SAVE_CONFIG] [--clear-cache]
[--cache-path CACHE_PATH] [--offline]
[--single-location SINGLE_LOCATION]
[--stackers [STACKERS ...]]
[--single-swap-locations [SINGLE_SWAP_LOCATIONS ...]]
plugin ...
volatility: error: Please select a plugin to runuser@TUSKEDEV ~ [2]> vol -h
Volatility 3 Framework 2.4.2
usage: volatility [-h] [-c CONFIG] [--parallelism [{processes,threads,off}]]
[-e EXTEND] [-p PLUGIN_DIRS] [-s SYMBOL_DIRS] [-v] [-l LOG]
[-o OUTPUT_DIR] [-q] [-r RENDERER] [-f FILE]
[--write-config] [--save-config SAVE_CONFIG] [--clear-cache]
[--cache-path CACHE_PATH] [--offline]
[--single-location SINGLE_LOCATION]
[--stackers [STACKERS ...]]
[--single-swap-locations [SINGLE_SWAP_LOCATIONS ...]]
plugin ...
An open-source memory forensics framework
options:
-h, --help Show this help message and exit, for specific plugin
options use 'volatility <pluginname> --help'
-c CONFIG, --config CONFIG
Load the configuration from a json file
--parallelism [{processes,threads,off}]
Enables parallelism (defaults to off if no argument
given)
-e EXTEND, --extend EXTEND
Extend the configuration with a new (or changed)
setting
-p PLUGIN_DIRS, --plugin-dirs PLUGIN_DIRS
Semi-colon separated list of paths to find plugins
-s SYMBOL_DIRS, --symbol-dirs SYMBOL_DIRS
Semi-colon separated list of paths to find symbols
-v, --verbosity Increase output verbosity
-l LOG, --log LOG Log output to a file as well as the console
-o OUTPUT_DIR, --output-dir OUTPUT_DIR
Directory in which to output any generated files
-q, --quiet Remove progress feedback
-r RENDERER, --renderer RENDERER
Determines how to render the output (quick, none, csv,
pretty, json, jsonl)
-f FILE, --file FILE Shorthand for --single-location=file:// if single-
location is not defined
--write-config Write configuration JSON file out to config.json
--save-config SAVE_CONFIG
Save configuration JSON file to a file
--clear-cache Clears out all short-term cached items
--cache-path CACHE_PATH
Change the default path
(/home/user/.cache/volatility3) used to store the
cache
--offline Do not search online for additional JSON files
--single-location SINGLE_LOCATION
Specifies a base location on which to stack
--stackers [STACKERS ...]
List of stackers
--single-swap-locations [SINGLE_SWAP_LOCATIONS ...]
Specifies a list of swap layer URIs for use with
single-location
Plugins:
For plugin specific options, run 'volatility <plugin> --help'
plugin
banners.Banners Attempts to identify potential linux banners in an
image
configwriter.ConfigWriter
Runs the automagics and both prints and outputs
configuration in the output directory.
frameworkinfo.FrameworkInfo
Plugin to list the various modular components of
Volatility
isfinfo.IsfInfo Determines information about the currently available
ISF files, or a specific one
layerwriter.LayerWriter
Runs the automagics and writes out the primary layer
produced by the stacker.
linux.bash.Bash Recovers bash command history from memory.
linux.check_afinfo.Check_afinfo
Verifies the operation function pointers of network
protocols.
linux.check_creds.Check_creds
Checks if any processes are sharing credential
structures
linux.check_idt.Check_idt
Checks if the IDT has been altered
linux.check_modules.Check_modules
Compares module list to sysfs info, if available
linux.check_syscall.Check_syscall
Check system call table for hooks.
linux.elfs.Elfs Lists all memory mapped ELF files for all processes.
linux.envars.Envars
linux.envvars.Envvars
Lists processes with their environment variables
linux.iomem.IOMem Generates an output similar to /proc/iomem on a
running system.
linux.keyboard_notifiers.Keyboard_notifiers
Parses the keyboard notifier call chain
linux.kmsg.Kmsg Kernel log buffer reader
linux.lsmod.Lsmod Lists loaded kernel modules.
linux.lsof.Lsof Lists all memory maps for all processes.
linux.malfind.Malfind
Lists process memory ranges that potentially contain
injected code.
linux.mountinfo.MountInfo
Lists mount points on processes mount namespaces
linux.proc.Maps Lists all memory maps for all processes.
linux.psaux.PsAux Lists processes with their command line arguments
linux.pslist.PsList
Lists the processes present in a particular linux
memory image.
linux.psscan.PsScan
Scans for processes present in a particular linux
image.
linux.pstree.PsTree
Plugin for listing processes in a tree based on their
parent process ID.
linux.sockstat.Sockstat
Lists all network connections for all processes.
linux.tty_check.tty_check
Checks tty devices for hooks
mac.bash.Bash Recovers bash command history from memory.
mac.check_syscall.Check_syscall
Check system call table for hooks.
mac.check_sysctl.Check_sysctl
Check sysctl handlers for hooks.
mac.check_trap_table.Check_trap_table
Check mach trap table for hooks.
mac.ifconfig.Ifconfig
Lists network interface information for all devices
mac.kauth_listeners.Kauth_listeners
Lists kauth listeners and their status
mac.kauth_scopes.Kauth_scopes
Lists kauth scopes and their status
mac.kevents.Kevents
Lists event handlers registered by processes
mac.list_files.List_Files
Lists all open file descriptors for all processes.
mac.lsmod.Lsmod Lists loaded kernel modules.
mac.lsof.Lsof Lists all open file descriptors for all processes.
mac.malfind.Malfind
Lists process memory ranges that potentially contain
injected code.
mac.mount.Mount A module containing a collection of plugins that
produce data typically found in Mac's mount command
mac.netstat.Netstat
Lists all network connections for all processes.
mac.proc_maps.Maps Lists process memory ranges that potentially contain
injected code.
mac.psaux.Psaux Recovers program command line arguments.
mac.pslist.PsList Lists the processes present in a particular mac memory
image.
mac.pstree.PsTree Plugin for listing processes in a tree based on their
parent process ID.
mac.socket_filters.Socket_filters
Enumerates kernel socket filters.
mac.timers.Timers Check for malicious kernel timers.
mac.trustedbsd.Trustedbsd
Checks for malicious trustedbsd modules
mac.vfsevents.VFSevents
Lists processes that are filtering file system events
timeliner.Timeliner
Runs all relevant plugins that provide time related
information and orders the results by time.
windows.bigpools.BigPools
List big page pools.
windows.cachedump.Cachedump
Dumps lsa secrets from memory
windows.callbacks.Callbacks
Lists kernel callbacks and notification routines.
windows.cmdline.CmdLine
Lists process command line arguments.
windows.crashinfo.Crashinfo
windows.devicetree.DeviceTree
Listing tree based on drivers and attached devices in
a particular windows memory image.
windows.dlllist.DllList
Lists the loaded modules in a particular windows
memory image.
windows.driverirp.DriverIrp
List IRPs for drivers in a particular windows memory
image.
windows.drivermodule.DriverModule
Determines if any loaded drivers were hidden by a
rootkit
windows.driverscan.DriverScan
Scans for drivers present in a particular windows
memory image.
windows.dumpfiles.DumpFiles
Dumps cached file contents from Windows memory
samples.
windows.envars.Envars
Display process environment variables
windows.filescan.FileScan
Scans for file objects present in a particular windows
memory image.
windows.getservicesids.GetServiceSIDs
Lists process token sids.
windows.getsids.GetSIDs
Print the SIDs owning each process
windows.handles.Handles
Lists process open handles.
windows.hashdump.Hashdump
Dumps user hashes from memory
windows.info.Info Show OS & kernel details of the memory sample being
analyzed.
windows.joblinks.JobLinks
Print process job link information
windows.ldrmodules.LdrModules
windows.lsadump.Lsadump
Dumps lsa secrets from memory
windows.malfind.Malfind
Lists process memory ranges that potentially contain
injected code.
windows.mbrscan.MBRScan
Scans for and parses potential Master Boot Records
(MBRs)
windows.memmap.Memmap
Prints the memory map
windows.mftscan.MFTScan
Scans for MFT FILE objects present in a particular
windows memory image.
windows.modscan.ModScan
Scans for modules present in a particular windows
memory image.
windows.modules.Modules
Lists the loaded kernel modules.
windows.mutantscan.MutantScan
Scans for mutexes present in a particular windows
memory image.
windows.netscan.NetScan
Scans for network objects present in a particular
windows memory image.
windows.netstat.NetStat
Traverses network tracking structures present in a
particular windows memory image.
windows.poolscanner.PoolScanner
A generic pool scanner plugin.
windows.privileges.Privs
Lists process token privileges
windows.pslist.PsList
Lists the processes present in a particular windows
memory image.
windows.psscan.PsScan
Scans for processes present in a particular windows
memory image.
windows.pstree.PsTree
Plugin for listing processes in a tree based on their
parent process ID.
windows.registry.certificates.Certificates
Lists the certificates in the registry's Certificate
Store.
windows.registry.hivelist.HiveList
Lists the registry hives present in a particular
memory image.
windows.registry.hivescan.HiveScan
Scans for registry hives present in a particular
windows memory image.
windows.registry.printkey.PrintKey
Lists the registry keys under a hive or specific key
value.
windows.registry.userassist.UserAssist
Print userassist registry keys and information.
windows.sessions.Sessions
lists Processes with Session information extracted
from Environmental Variables
windows.skeleton_key_check.Skeleton_Key_Check
Looks for signs of Skeleton Key malware
windows.ssdt.SSDT Lists the system call table.
windows.statistics.Statistics
windows.strings.Strings
Reads output from the strings command and indicates
which process(es) each string belongs to.
windows.svcscan.SvcScan
Scans for windows services.
windows.symlinkscan.SymlinkScan
Scans for links present in a particular windows memory
image.
windows.vadinfo.VadInfo
Lists process memory ranges.
windows.vadwalk.VadWalk
Walk the VAD tree.
windows.vadyarascan.VadYaraScan
Scans all the Virtual Address Descriptor memory maps
using yara.
windows.verinfo.VerInfo
Lists version information from PE files.
windows.virtmap.VirtMap
Lists virtual mapped sections.
yarascan.YaraScan Scans kernel memory using yara rules (string or file).然而,这些写不进PPT里,因为长得很,且要用到的模块很少,例如Linux,在座的除了我在用Arch,还有其他人吗?连tm搞个原神都得找安装脚本,甚至还得烧三炷香
PPT咋设计
因PPT只是用来展示的,故使用LibreOffice以达到更好的体验,毕竟隔壁WPS那边……模板一个个神tm跟政府工作报告似的……
3月31日的分享会PPT设计我觉得挺好的,直接找了个相似的套上去了
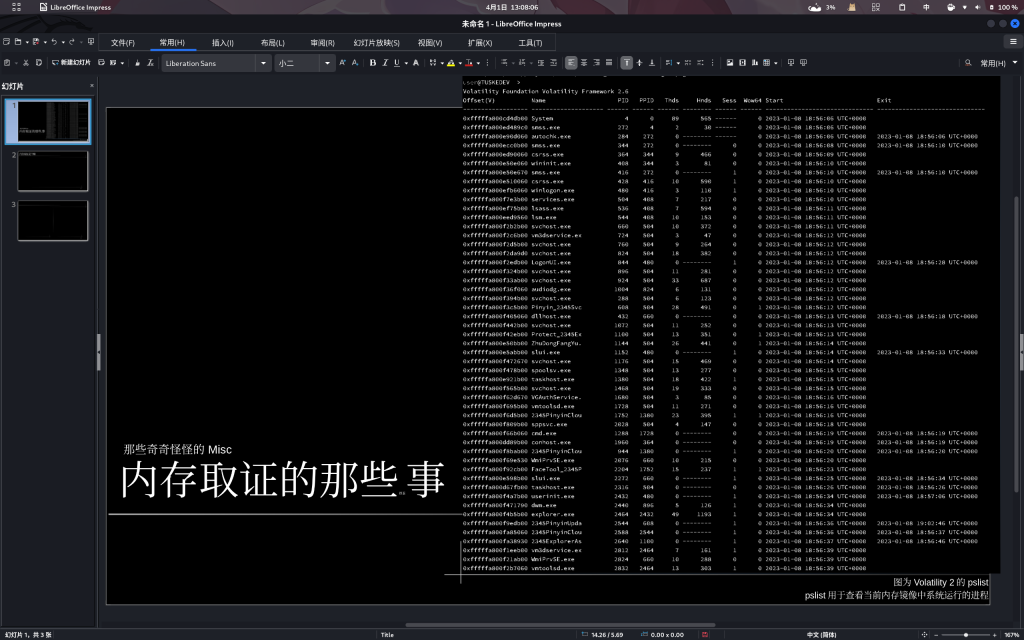
因为我实在不知道内存取证这玩意儿该怎么配图,干脆直接拿writeup的图得了
怎么串起逻辑
我个人计划是先一笔带过我接触的Misc的样子,第一反应是东北大乱炖,后面发现不太有冲击力,遂换成铁锅炖或天津的大饼夹一切(我手上没有相关图片,故放弃,这玩意儿要例子的话直接津云/北方网上找)。
然后是介绍内存取证是啥(解释清楚的话我个人认为也可以一笔带过),之后说明工具和用法(主要是俩volatility,因为用法不同且主要),然后通过题目带入通用思路(顺便说明一下如何)。因为这玩意儿主要是面向CTF的,所以如何提取镜像也是一笔代过。
如何讲述
第一页后,这里插个题外话,这是我眼中的Misc和其中的隐写,这也是为什么我会在这里说内存取证而非隐写的主要原因。
第三页(介绍)
一笔带过,因为只是引入。基本上读下上面写的就够了。
第四页(提取镜像软件)
主要介绍DumpIt,顺便抛几个冷提醒。顺带一提,Windows蓝屏错误会自动dump内存,在根目录生成一个名叫memory.dmp文件,那玩意儿可以用WinDbg分析。
第五页(分析镜像软件)
没得说,Volatility,可参考小约翰可汗开头介绍硬核狠人的语气,动画可参考MacOS 8的OOBE。下面让我们介绍,分析内存的最常用软件,更新大版本附赠重新学习大礼包的典范,Volatility。
第六页(Volatility用法)
看个乐呵就得了,没必要那么较真。看几秒就得了,基本操作而已。
第七、八页(Volatility插件)
这个没话可说,看两三秒得了,反正没啥大用,因为可以运行volatility -h(2)或vol -h(3),具体用啥直接填上去就得,即将下海的蔡英文都能会的那种。我想你们肯定会骂为什么字那么小,那是因为……这些东西根本不需要记……
第九页
上手实操,没啥可说的。接下来实操环节。
首先打开terminal跑俩命令,./volatility -h和./volatility –info当说明书摆旁边。(如果不知道后面的版本号啥意思,自行BetaWorld Wiki,这句话只会在有人问起的时候回复。)
然后开nautilus找到文件用GHex打开。顺便提一嘴,如果你们不知道这文件是嘛的时候,直接看二进制。慢慢滚,找到特定字符串后猜测它是什么。看这些字符,像不像Windows的内存镜像。然后找另一个特定字符串确认是Windows的内存镜像。
接下来再开个terminal,好,拿Volatility 2分析这个镜像。我们首先应该跑一遍imageinfo,因为我们并不知道这个镜像需要拿哪个profile跑。然后发现有多个建议的profile,这里有多个推荐的profile,这主要是因为这些系统都是NT 6.1内核,一般取第一个作为首选。
然后运行./volatility -f flag.raw –profile=Win7SP1x64后ctrl-c终止运行,留在终端历史备用。我目前的思路是这样的:首先看看桌面上有啥,然后一步一步走着。
左侧是备用的说明书,在说明书里寻找相应模块。GNOME terminal(GTK 3版)右上角有搜索工具用于寻找单词。因为我目前需要看看桌面上有啥,所以我需要寻找screenshot这个单词。然后找到了screenshot – Save a pseudo-screenshot based on GDI windows,翻译出来就是这个模块主要作用是保存一个基于GDI的伪截图。什么是GDI?上搜索引擎。读一下wiki第一句话就行。
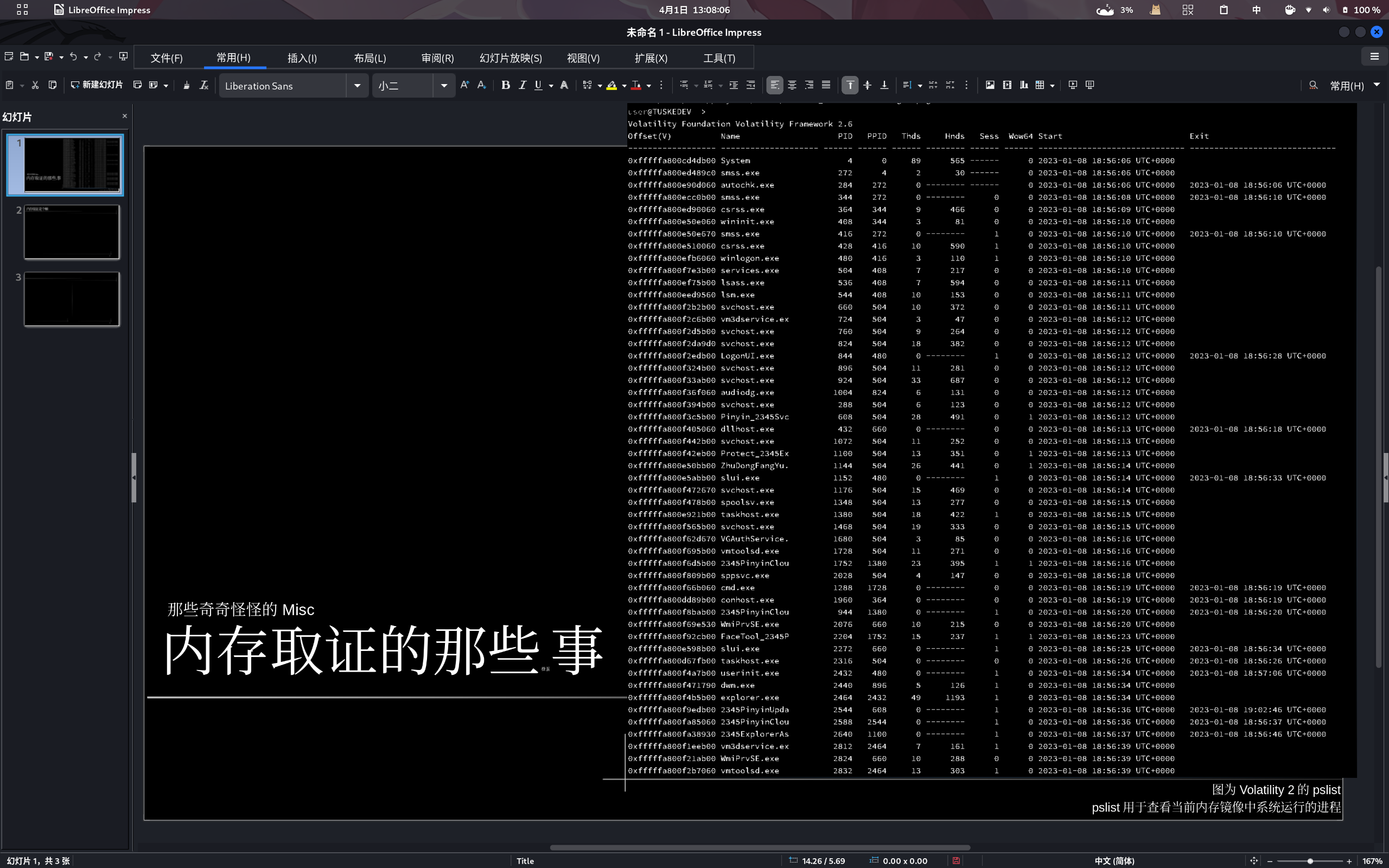
然后生成一个screenshot,提前另外设定一个目录用于保存这些截图。打开nautilus寻找这些截图。咱们看一下这些伪截图。你看这张截图有字,看起来很抽象,但至少它像个桌面。标题栏有字,上面写着dumpit,且镜像生成于3:03,后面应该是资源管理器,打开了C盘……
然后是看看dumpit这个进程是个嘛。既然要看进程,首先得找找它的进程编号P(rocess )ID,我们继续在说明书找带process的内容。看看里面有什么好康的。2345拼音,主动防御……好嘛这系统简直没法要了,哪个傻缺要在屎里淘金啊……好嘛还有个360,这是打算以毒攻毒吗……好了找到了dumpit,PID为2052,PPID为2464。
然后我们需要dump出来这个损玩意儿,继续说明书找。好我们找到了个叫memdump的玩意儿,它能将这个进程所在的内存给提取出来。如果你们不知道怎么操作,直接裸跑就行。你看,它报了个错,说是少了–dump-dir指令。补上后运行,此时它会逐个dump进程。当然实际上根本不需要这么多,我们实际是可以指定pid的,加个-p加pid号就行。这里这么干是为了假装我一脸懵逼。
这里我们再引入一个指令叫strings,它是用来寻找文件内部的字符串的。在左侧跑下strings -h,看看它能干什么。
好的那咱们在右侧分别看看对应进程。这里跑strings *.dmp,通个管道给grep筛一下,然后再导出到一个文件。然后我们要筛什么呢?咱们重新看下题目。关键词:秘密secret,还有典中典flag。各自跑一遍。secret倒是没找出什么。flag那边卧槽一团乱麻,跟尼玛我桌子似的。干脆直接针对性打击DumpIt。你看,介不就flag。
现存什么问题
第一稿
太短,讲不到40min
隐写
为什么要挖出这个坟
很简单,另一个人让我上去讲几句。因为没有指定方向,故挖坟。
预计时间
20分钟。
彩蛋:那些奇奇怪怪的关系
有时候隐写真能用在某些奇奇怪怪的地方上……
虽然……没啥大用,因为有些平台默认压图……
所以……不如……
反正没人看懂,对吧(
筛选用户了属实是(虽然从TG @TuskedEvening0 也能找到我,虽然这样Garden Chen那边也能看到(没啥大事
对应啥题
- NewStarCTF 2023 Week1 Misc 隐秘的眼睛(SilentEye)
- NewStarCTF 2023 Week1 Misc 机密图片(LSB隐写)
- NewStarCTF 2023 Week2 Misc Jvav(Java盲水印)
- NewStarCTF 2023 Week4 Misc 依旧是空白(SNOW隐写+JPG爆破宽高)
- NewStarCTF 2023 Week4 Misc R通大残(图片像素RGB值提取)
然而肯定不止这些,因为光我从别人手里拿到的工具就比这些题*3还要多。
而且不止这些。BiliBili上搜索“R6SLAB”,你能搜到好多基于各种奇奇怪怪的方案的彩虹六号直播方案。
什么特征
又杂又乱,甚至根本找不到切入点。
那咋办?设置个情景引入吧。
原定情景引入
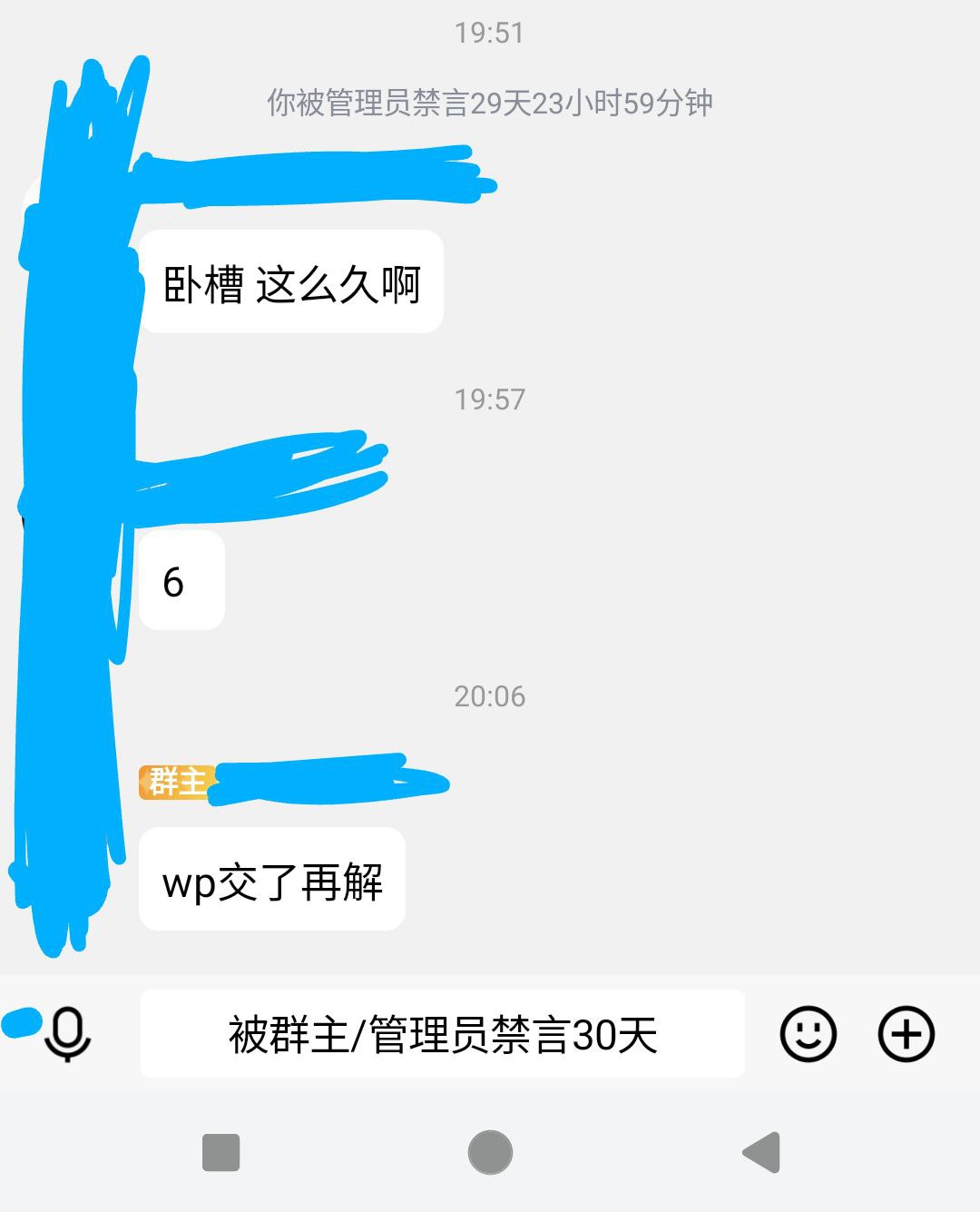
因为一些特殊原因,我只能在写完那五周的WriteUp才能在群里发言。但是我不想去写那么多,然后我想到了贿赂某个管理。鉴于那个管理和群主一个宿舍,直球贿赂有被群主发现的风险。
所以我得用点隐写。
粗略该讲啥
因时间所限,我个人选择其中一种方案进行演示,其余均为讲题环节,切入点实际上极其混乱。实际上跟念WriteUp屁区别没有。也许下次就该试试讲点pwn和reverse了,但是还没入门,而且是下一个图文的预计内容。
该用什么图演示
- Pixiv 110011602
- 微信聊天记录
- BV1GM4y1b7JB 00:35
这张图同时也是题图。
侧重点在哪
如果真是和念WriteUp一样,那不如直接念得了,用不着写这篇文章。所以这篇稿件最应该侧重于原理解说。
内容来源?
很简单,NewStarCTF。
PPT如何设计及具体如何讲述
以下使用软件为LibreOffice。
第一页/封面
因为原PPT丢了,所以图片来源直接贴上面了。
附注,改了仨字,顺便改成了4:3。
其实这个题图后续也是有用的。
第二页/情景引入
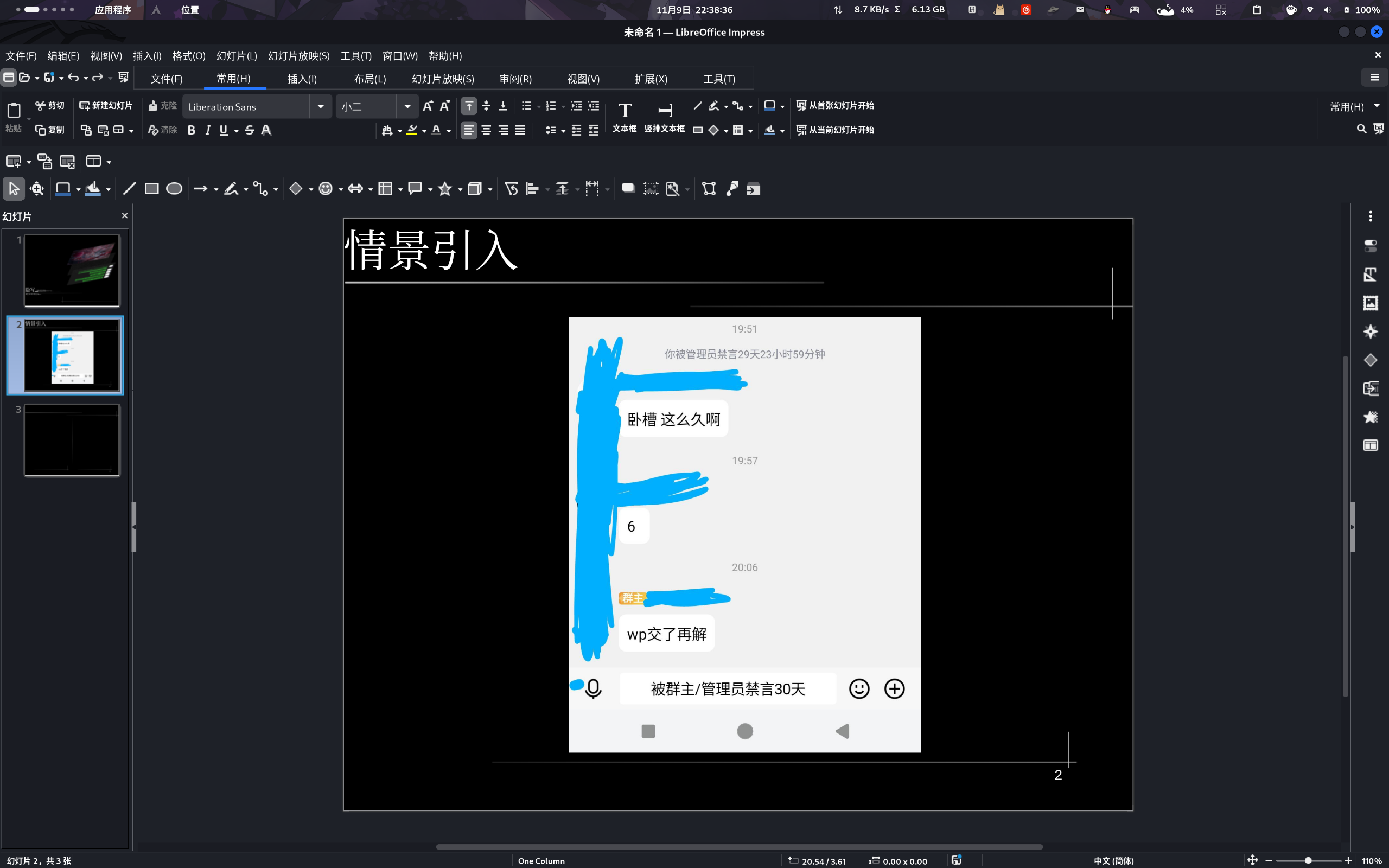
拿自己开涮先。犹记得一个月前,*神曾禁了我30天言,等写完NewStarCTF除misc外的任意一个方向的所有周的WriteUp才能解封。这工作量想想都大,毕竟你抄人家现有打法糊弄,人家可能还会加码30天。加上我身上屁事一堆,那只能找其他人说情呗。然后就是题图里说的事情了。
第三页/介绍内容
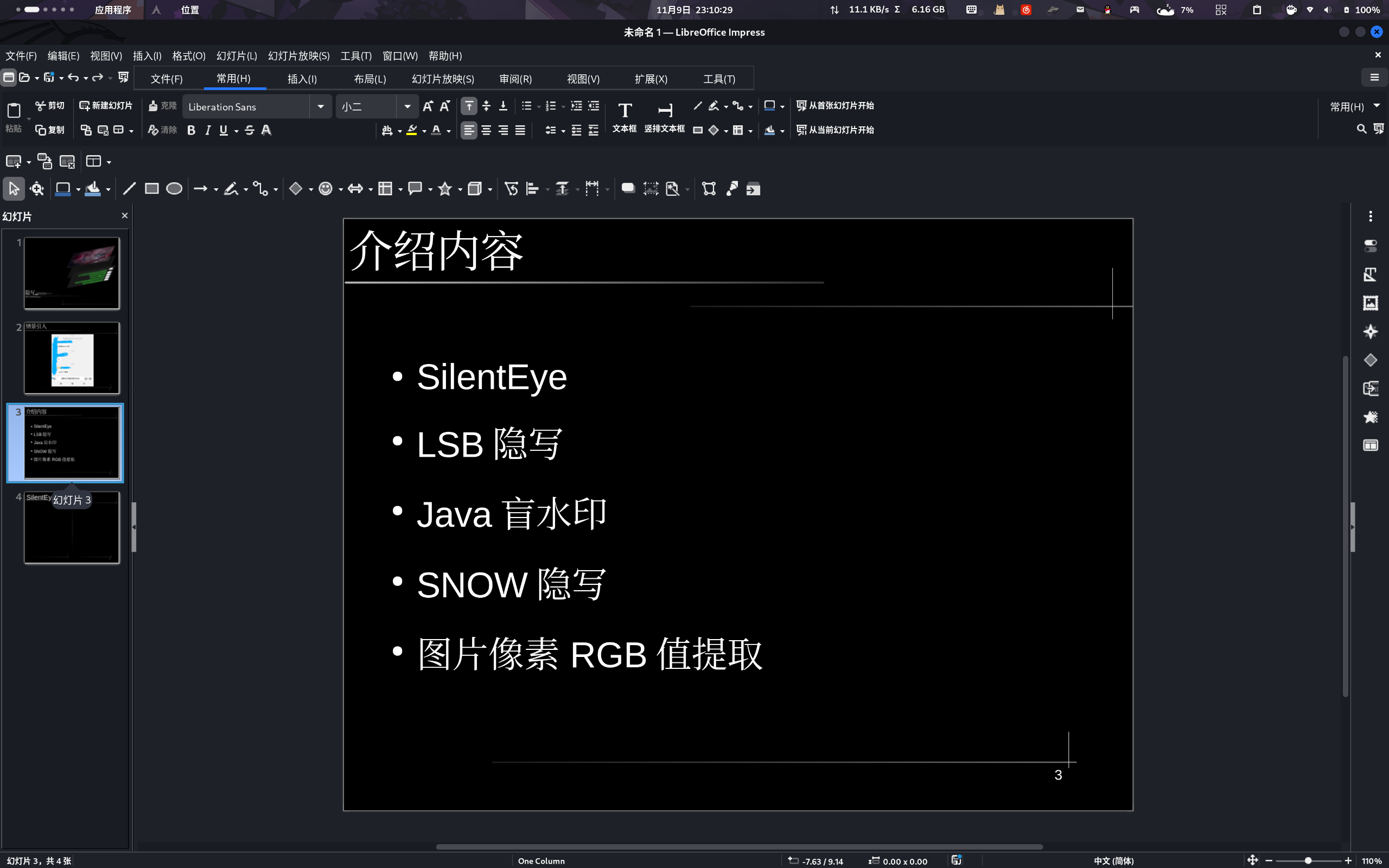
因时间所限,我只说这些,全部取自已经完事的NewStarCTF,你可以看作是2K23似的拙劣换皮。但是这里我会花更多的时间去讲原理,因为题解已经有人讲过了,我再讲一遍没有任何意义,甚至不如隔壁EA的Switch版FC Sports 24。
第四-六页/LSB隐写
附注,我特意和一个内容对调了,因为后者依赖前者。
第四页/LSB是什么
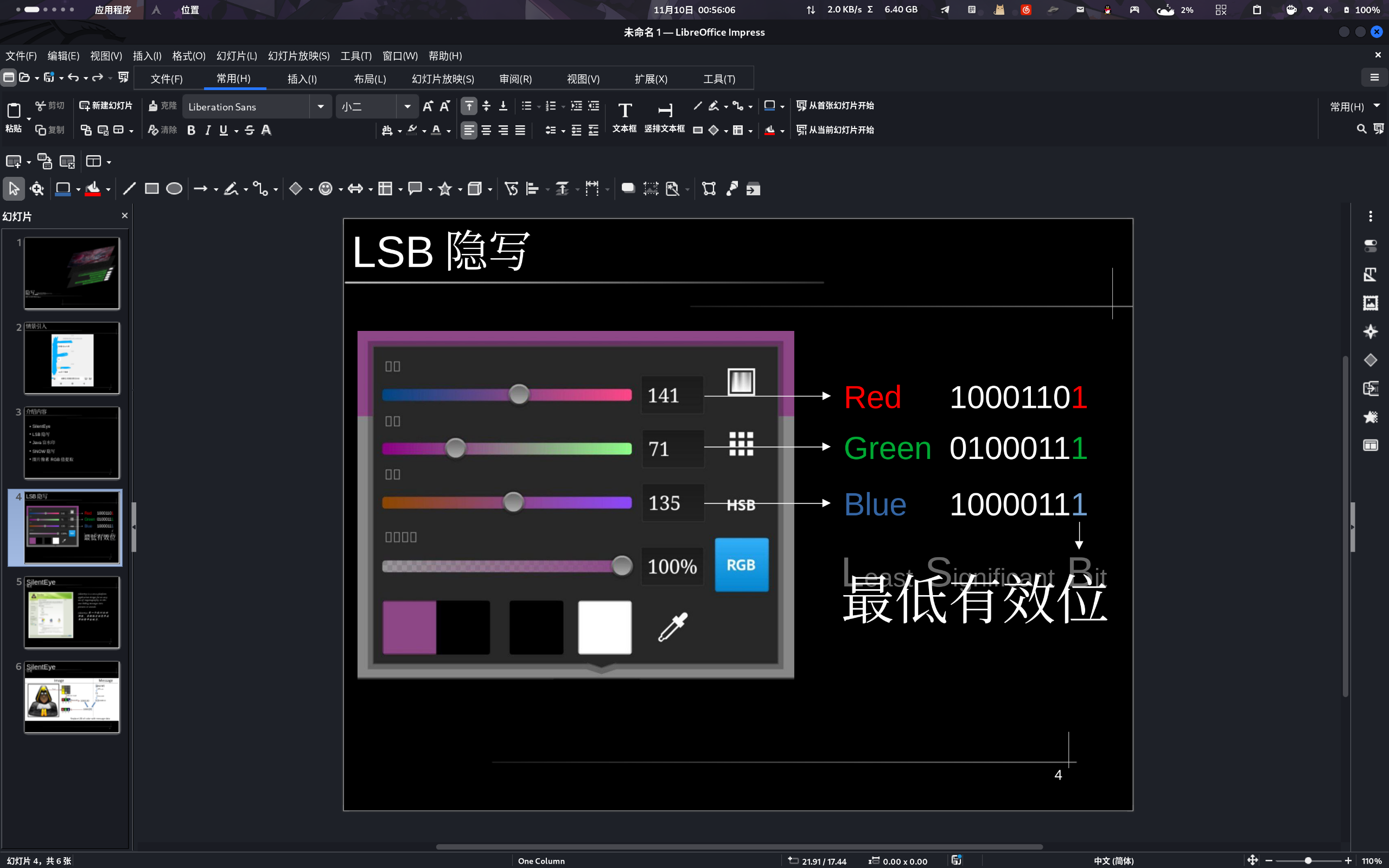
这是我在PS Touch里截的一张图,其中操作图像的最低单位是一个像素,该像素拥有它自己的RGB值,默认我们是以十进制输入它的,它实际存储的是其二进制值,这些8位二进制值的最后一位就是最低有效位,简称LSB。至于为什么刻意遮挡全称,记下来没用。
第五页/为什么LSB可以用于隐写
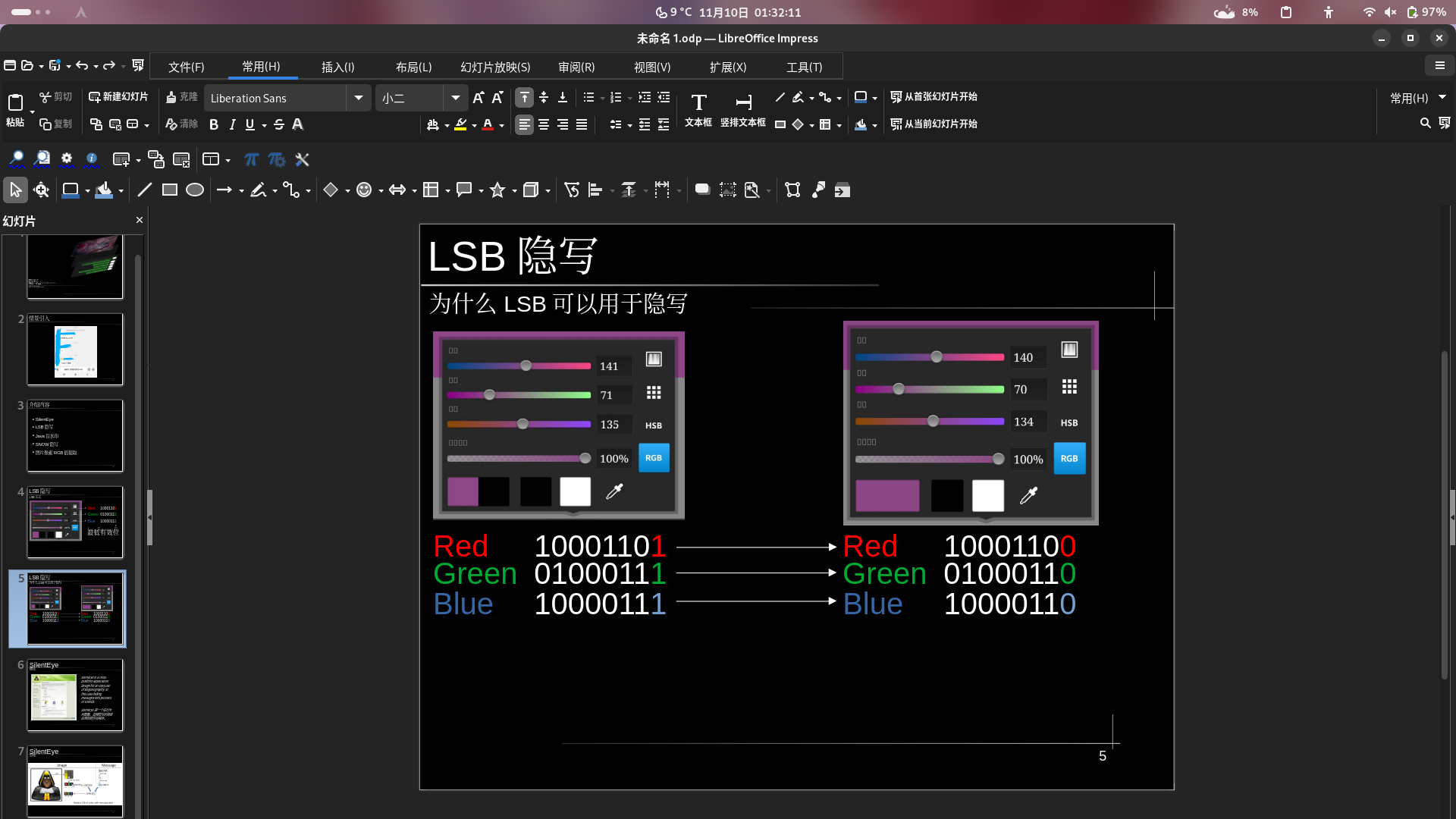
来来来,哥哥们姐姐们,你认为这俩色你分的出来吗?如果你能,你就是这个👍🏻。我想但凡是个人都分不清这俩玩意儿的区别。
第六页/怎么读取其中的信息
https://github.com/Giotino/stegsolve/
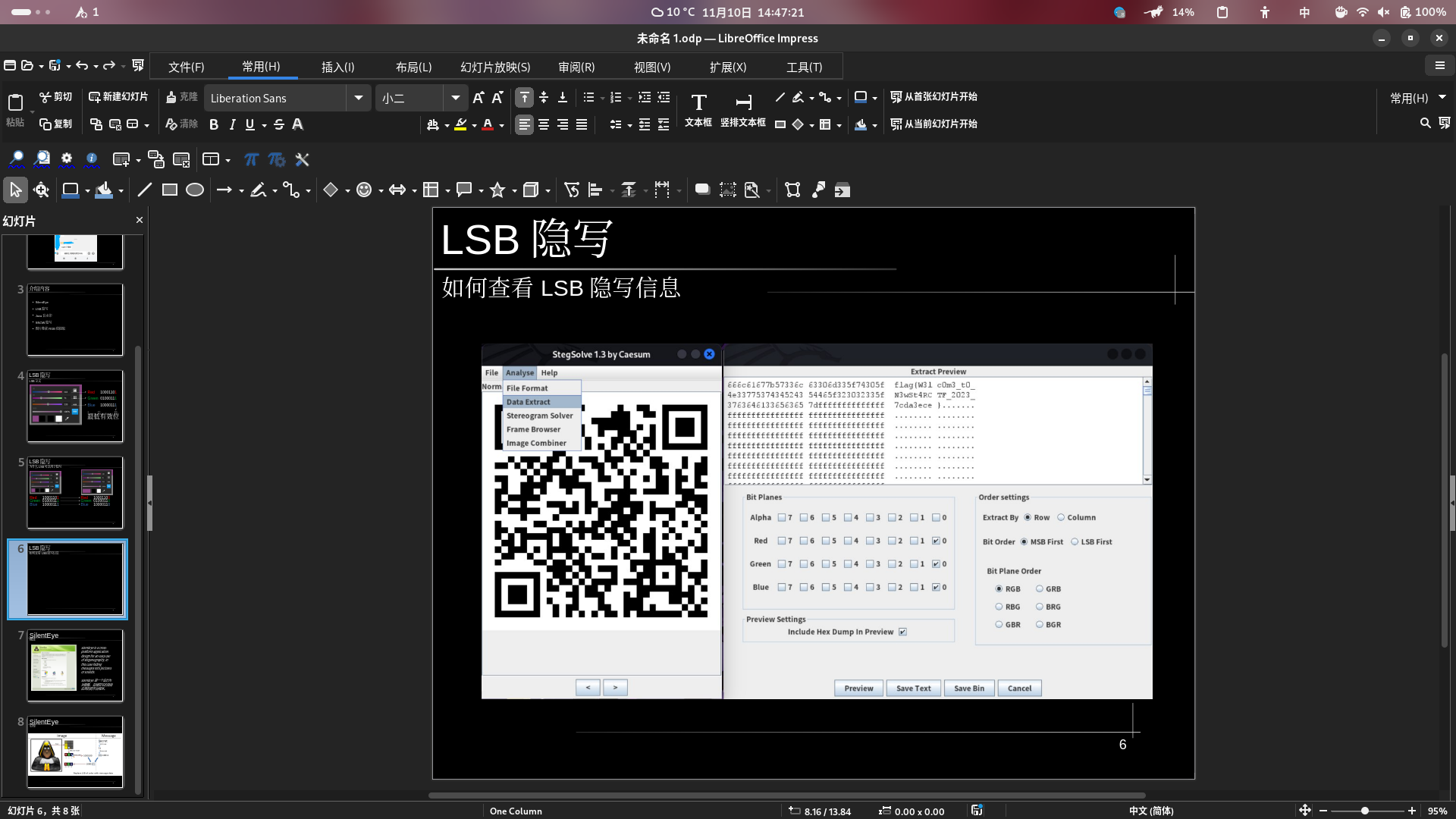
如图。
第七-八页/SilentEye
第七页/SilentEye是什么
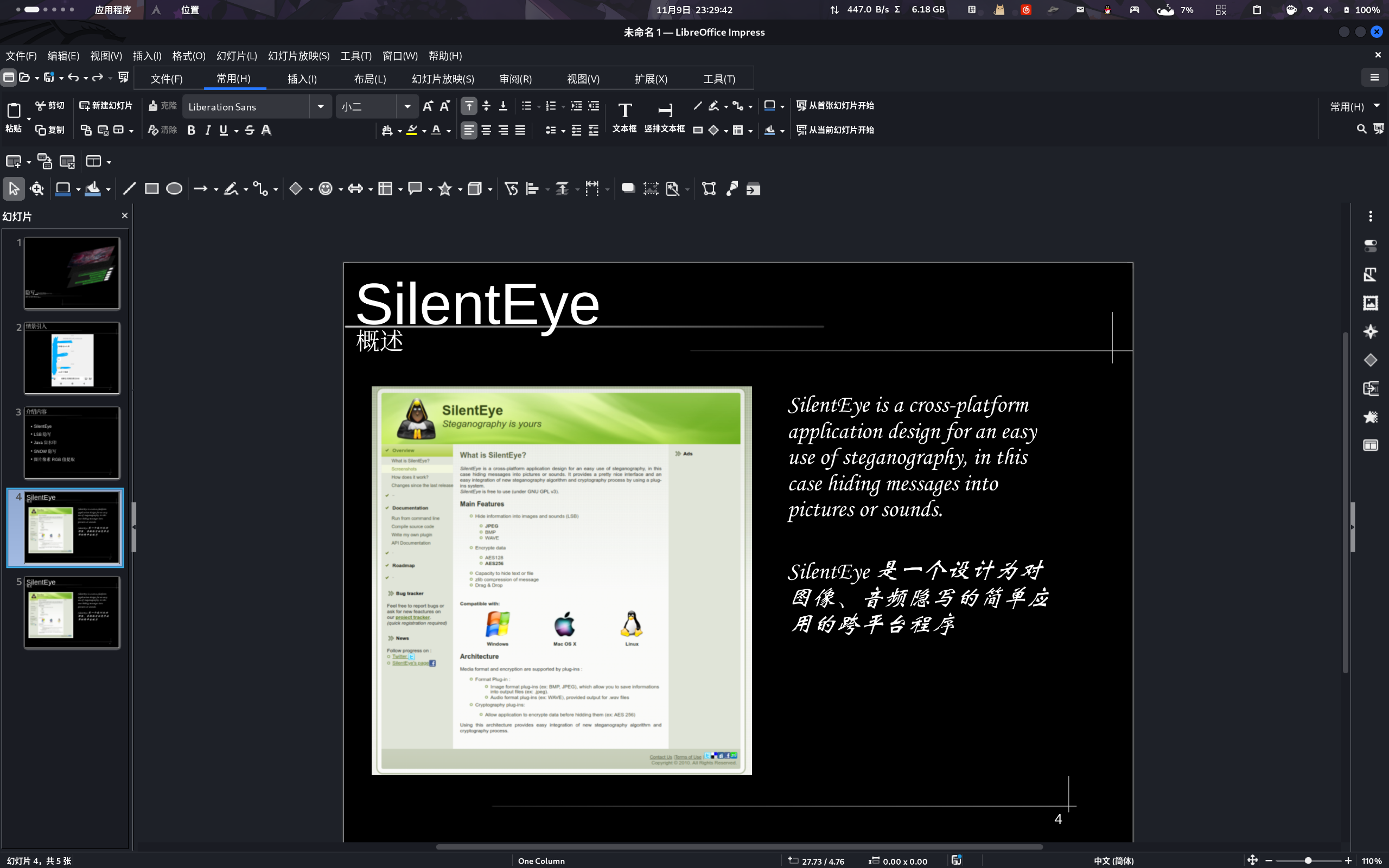
这页看看就得了,水一下时长。纯粹取自于其官网。
第八页/SilentEye原理
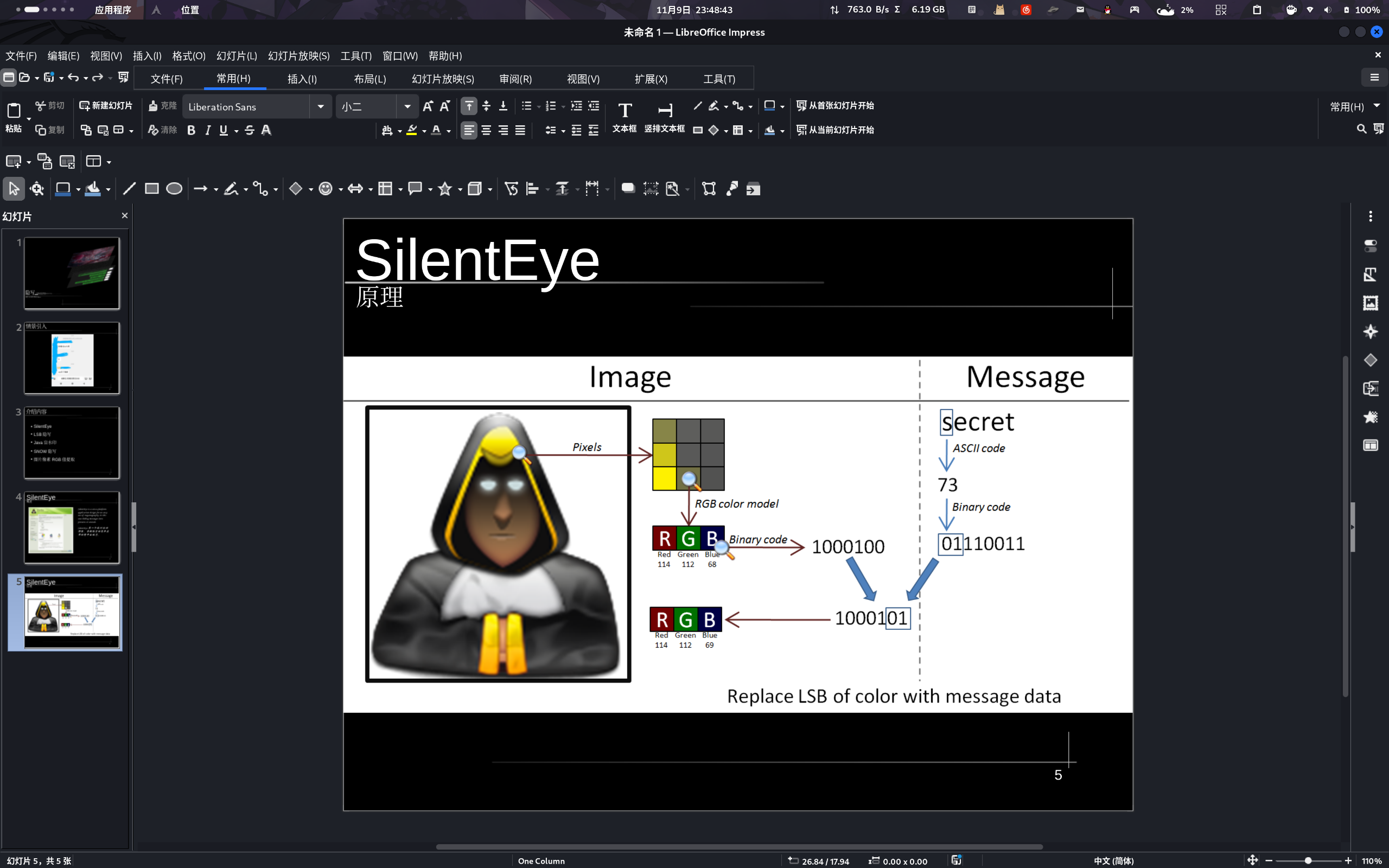
其实跟LSB隐写原理基本相同,只是被隐写数据处理的方法不同。
第九-十页/盲水印
导向 https://zhuanlan.zhihu.com/p/33526455 。
第九页(原理):盲水印原理自己看吧,我高数不好。你实际也不会去自己实现的,因为网上有现成脚本。NewStarCTF官方题解用到了一个Java实现。
第十页(特性):这个自己看看得了。哦对了,鲁棒性可以简单的理解为抗破坏性或可靠性,在直言trigger的某个视频里有提到过。
第11页/SNOW概述
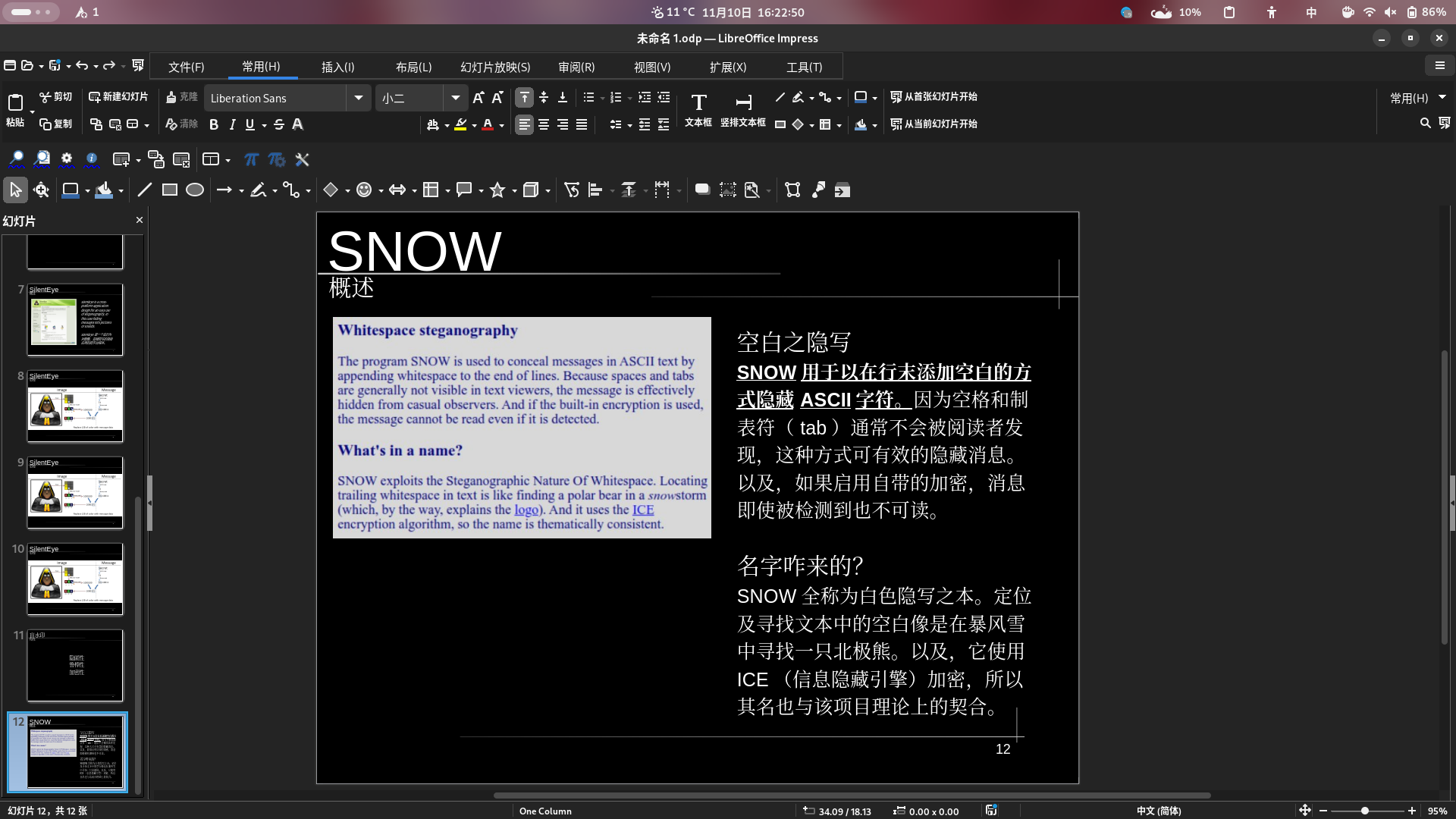
只需读下划线内容即可。需注意,部分翻译没有官方译名,由我进行翻译,不代表官方观点,也可能不契合原文含义。
文章的局限性
因写作时间过度紧张,我无法把一些东西塞进去,也无法做到其百分百准确和普适。
现存问题
很明显,太短,明显达不到预定的20分钟。
而且,因为刚刚招新,纯理论这条路是走不通的,已有人反馈听不懂。
选题也有重大问题,过度宽泛导致稿件难产,连带着各种准备不足,以至于最多的评价是“抽象”。

发表回复